Summary: Hackers are exploiting a security vulnerability in the Elementor Pro website builder plugin for WordPress, which is estimated to be used on over 12 million sites. The flaw allows attackers to create an account with administrator privileges and potentially take over a WordPress site. Users are advised to update to the latest version of the plugin to mitigate the risk of potential threats.
Unknown attackers are exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress, putting millions of sites at risk. The flaw affects versions 3.11.6 and earlier and was fixed by the plugin maintainers in version 3.11.7. The vulnerability is a case of broken access control, allowing an authenticated attacker to take over a WordPress site that has WooCommerce enabled, giving them administrator privileges. Users of the plugin are urged to update to version 3.11.7 or 3.12.0 as soon as possible.
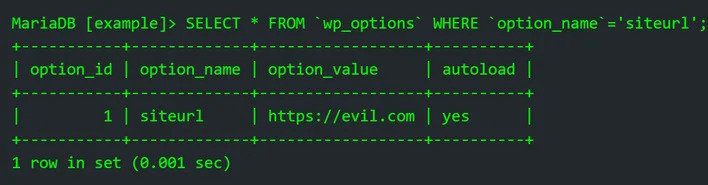
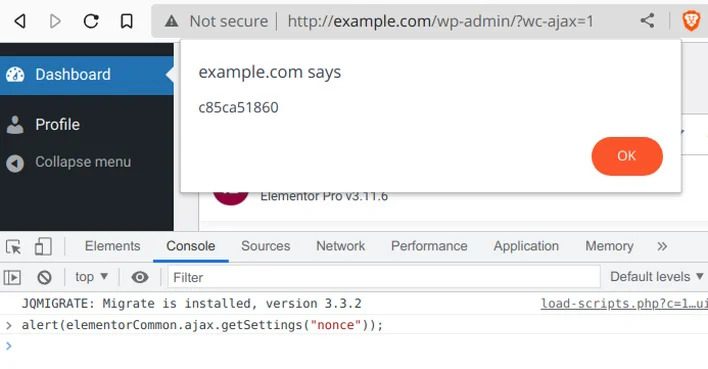
NinTechNet security researcher Jerome Bruandet discovered and reported the vulnerability on March 18, 2023. Patchstack has noted that the flaw is being exploited in the wild from several IP addresses, with attackers attempting to upload arbitrary PHP and ZIP archive files. If exploited, a malicious user could turn on the registration page (if disabled) and set the default user role to administrator. This would allow them to create an account that instantly has the administrator privileges. They could then redirect the site to another malicious domain or upload a malicious plugin or backdoor to further exploit the site.
This is not the first time a vulnerability has been discovered in an Elementor plugin. The Essential Addons for Elementor plugin was found to contain a critical vulnerability that could result in the execution of arbitrary code on compromised websites. WordPress also issued auto-updates to remediate another critical bug in the WooCommerce Payments plugin that allowed unauthenticated attackers to gain administrator access to vulnerable sites.







![How to enable dark mode on Instagram [year] 11 2025 Instagram dark mode guide](https://techtout.com/wp-content/uploads/2023/01/dark-mode-instagram-120x86.jpg)
![Best Metal Gaming Laptops [year] 12 2025 Best metal body laptops on Amazon](https://techtout.com/wp-content/uploads/2023/05/best-metal-gaming-laptops-120x86.jpg)
![25 popular Linux distros [year] 13 2025 Most popular Linux distros in 2023](https://techtout.com/wp-content/uploads/2023/08/popular-linux-distros-120x86.jpg)
![Instagram story decoration Ideas in [year] 14 2025 A photo of a person using Instagram on iPhone, showing Instagram stories decorations](https://techtout.com/wp-content/uploads/2023/02/decorate-instagram-stories-120x86.jpg)
![10 Best Browsers for iPhone in [year] 15 2025 Best iPhones browsers](https://techtout.com/wp-content/uploads/2023/05/best-iphone-browsers-120x86.jpg)
![Top 9 lifestyle apps that will improve the quality of your life in [year] 16 2025 Lifestyle apps for IOs and Android users](https://techtout.com/wp-content/uploads/2023/07/top-lifestyle-app-120x86.jpg)


![11 Latest Instagram Tips and Tricks [year] 20 2025 high angle photo of a mobile](https://techtout.com/wp-content/uploads/2020/08/instagram-profile-scaled-1-120x86.jpg)








